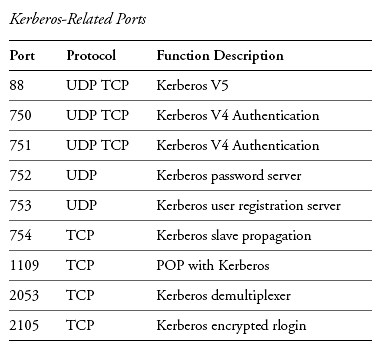
Kerberos Port | Overview Of Service Principal Name And Kerberos Authentication In Sql Server
If you choose the second one you may not need to do that. 88 Kerberos 750 Kerberos 389 Ldap 53 DNS 137 netbios Attention Il faut.
Datafusion Wiki Kerberos Tutorial
If you choose the first one you may need to have port 88 open on the firewall.
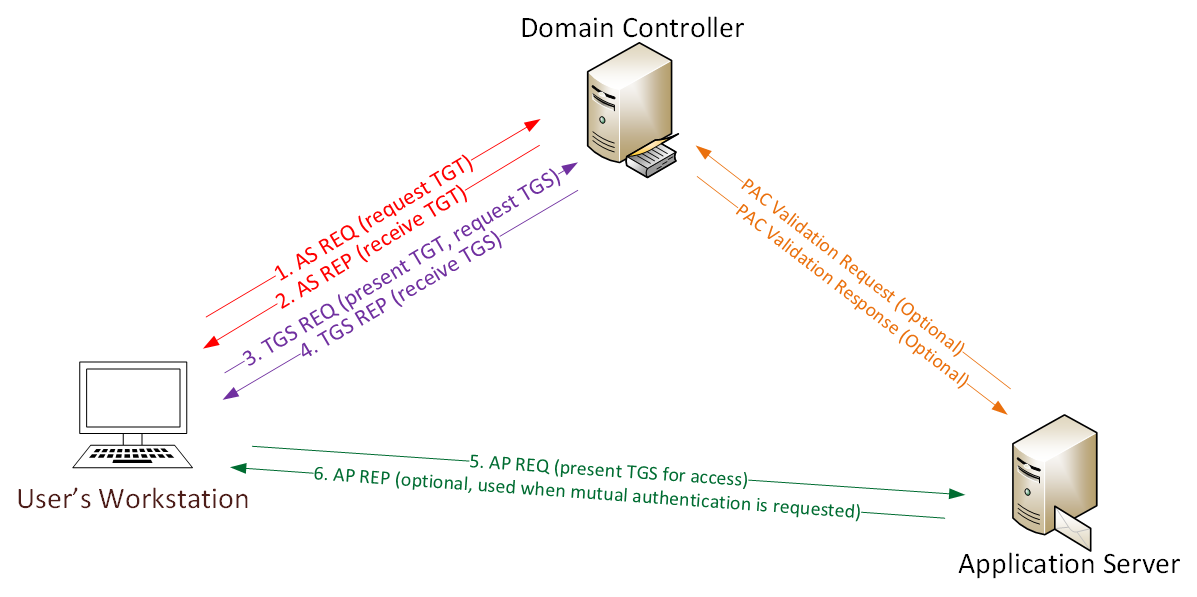
Kerberos port. If you choose the first one you may need to have port 88 open on the firewall. Microsoft-DS for Server Message Block SMB over IP traffic. Lightweight Directory Access Protocol LDAP ping.
Because of the inherent flaws in the Kerberos 4 protocol it is not recommended that you open Kerberos. It coexists with the NTLM challengeresponse protocol and is used in instances where both a. 3074 TCPUDP 53 TCPUDP 80 TCP 88 UDP.
Use Kerberos only Use any authentication protocol. Voici un récapitulatif des ports utilisés par lauthentification NTLM. Setspn -d ServiceClass Host.
Kerberos is primarily a UDP protocol although it falls back to TCP for large Kerberos tickets. TCP445 and UDP445. Xbox One LIVE ports.
Note the default port used by the designated Kerberos KDC. Celui-ci est utile lorsque vous devez autoriser un proxy qui est en DMZ Privée Non accessible dInternet à accéder à vos AD. The following table lists the default port used by the designated Kerberos KDC.
In this platform Kerberos provides information about the privileges of each user but it is responsability of each service to determine if the user has access to its resources. For more information about Protocol Transition with Constrained Delegation Technical Supplement please refer to the following article. Use Kerberos only Use any authentication protocol.
Kerberos authentication HTTP TCP. RPC for LSA SAM NetLogon 49152-65535TCPUDP. Setspn -s serviceClassHostPort AccountName.
Strictly speaking the only port that needs to be open for Kerberos to function properly is 88. The Windows Kerberos authentication package is the default authentication package in Windows Server 2003 in Windows Server 2008 and in Windows Vista. For more information about Protocol Transition with Constrained Delegation Technical Supplement please refer to the following article.
445 SMB 389 Ldap 88 Kerberos 750 Kerberos Ports UDP. It uses secret-key cryptography and a trusted third party for authenticating client. Kerberos is used in Active Directory.
Certificate-based authentication HTTPS TCP. TCP88 and UDP88. UserComputer login and authentication.
A range of RPC ports which should be restricted when. The default ports used by Kerberos are port 88 for the KDC 1 and port 749 for the admin server. The other ports can be opened as needed to provide their respective services to clients outside of the firewall.
The default ports used by Kerberos are port 88 for the KDC 1 and port 749 for the admin server. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. 3074 TCPUDP 53 TCPUDP 80 TCP 88 UDP 500 UDP 3544 UDP 4500 UDP.
You can however choose to run on other ports as long as they are specified in each hosts etcservices and krb5conf files and the kdcconf file on each KDC. Client Ports Server Port Service. Random port number between 49152 and 65535.
If your on-site users inside your firewall will need to get to KDCs in other realms you will also need to configure your firewall to allow. This may require special configuration on firewalls to allow the UDP response from the Kerberos server KDC. The following protocols and ports are required.
To delete an SPN run the following command at a command prompt. But if you notice a machine with port 88 Kerberos open you can be fairly sure that it is a Domain Controller. If you choose the second one you may not need to do that.
Xbox 360 LIVE ports. Kerberos clients need to send UDP and TCP packets on port 88 and receive replies from the Kerberos servers. The default port for the admin server is 749.
KDC Kerberos key distribution center server. TCP Port 139 and UDP 138 File Replication Service between domain controllers.
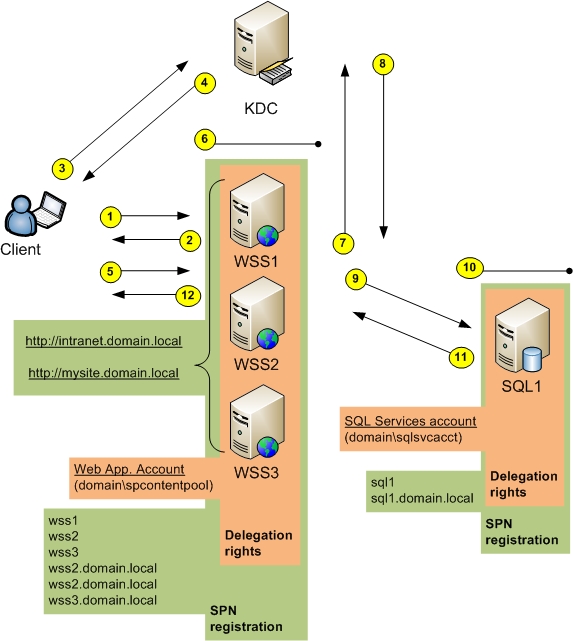
Kerberos In A Sharepoint Environment
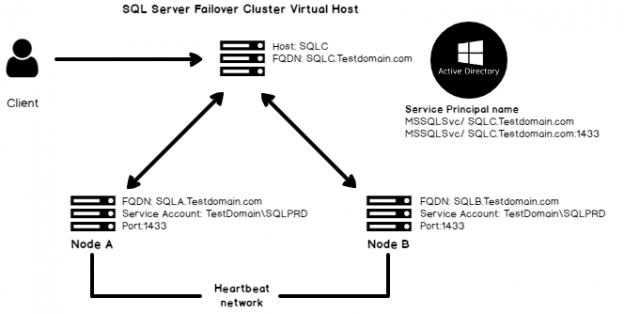
Overview Of Service Principal Name And Kerberos Authentication In Sql Server
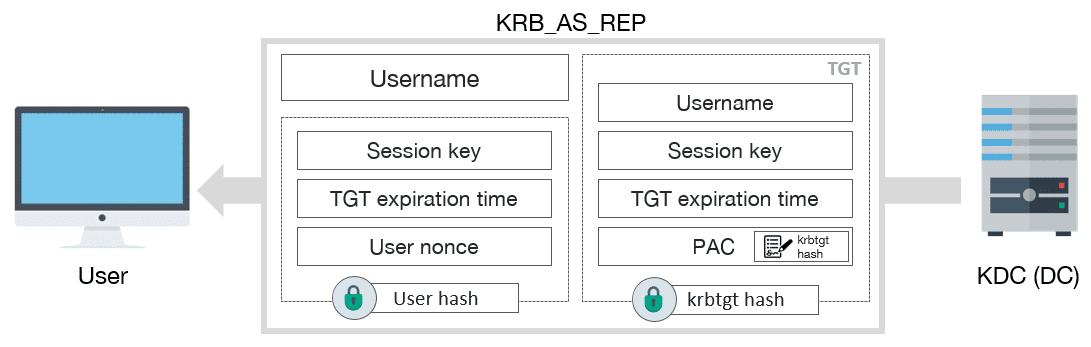
Kerberos I How Does Kerberos Work Theory
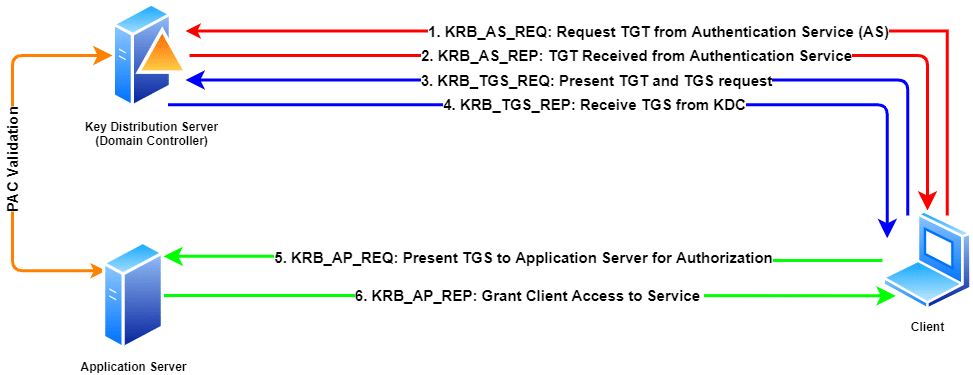
What Is Kerberos Understanding Kerberos What Is It How Does It Work
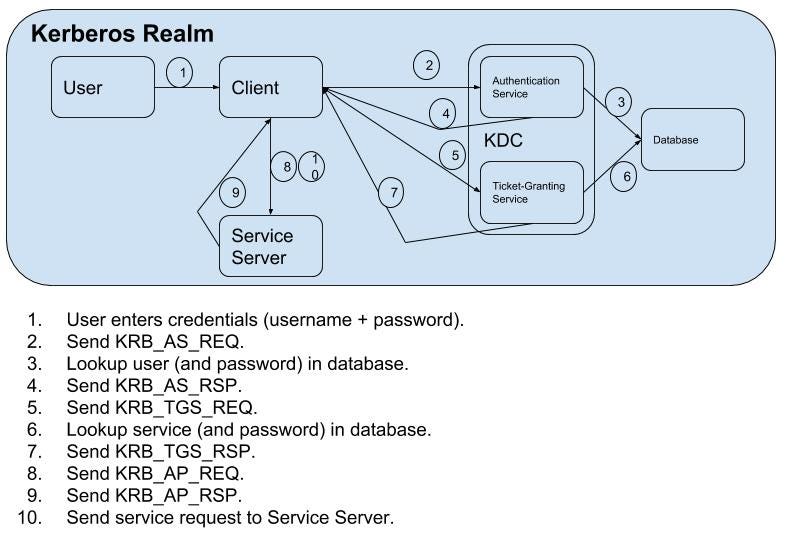
Kerberos And Windows Security Kerberos V5 Protocol By Robert Broeckelmann Medium

Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security
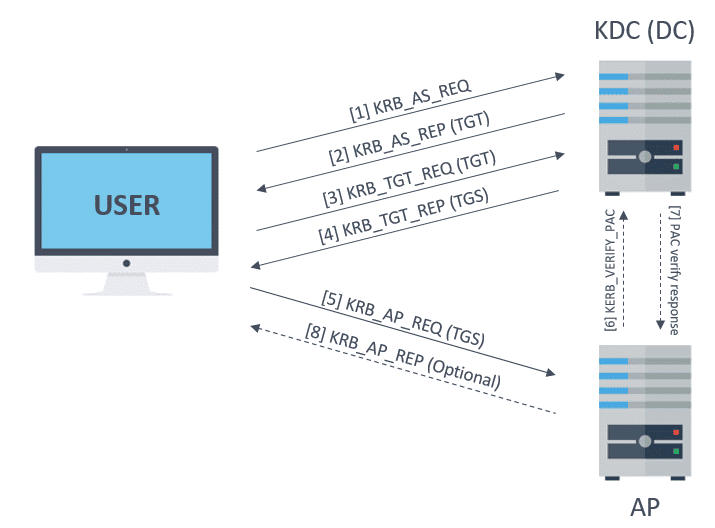
Kerberos I How Does Kerberos Work Theory

Windows Event Id 4771 Kerberos Pre Authentication Failed Adaudit Plus
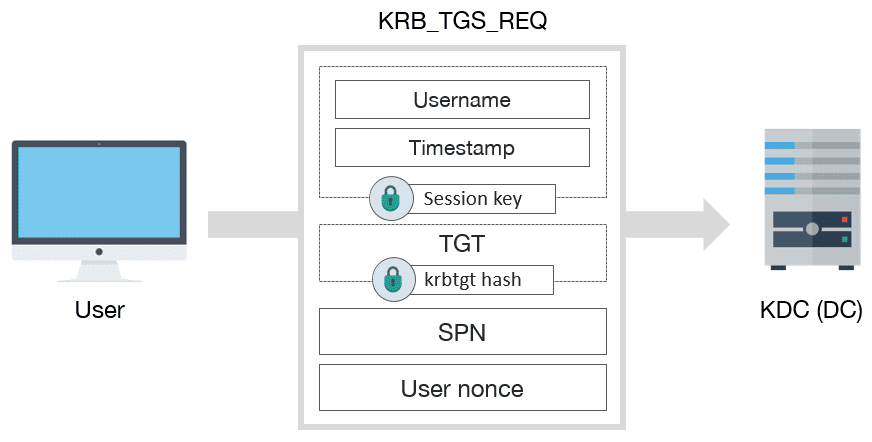
Kerberos I How Does Kerberos Work Theory
Understanding Kerberos Double Hop Microsoft Tech Community
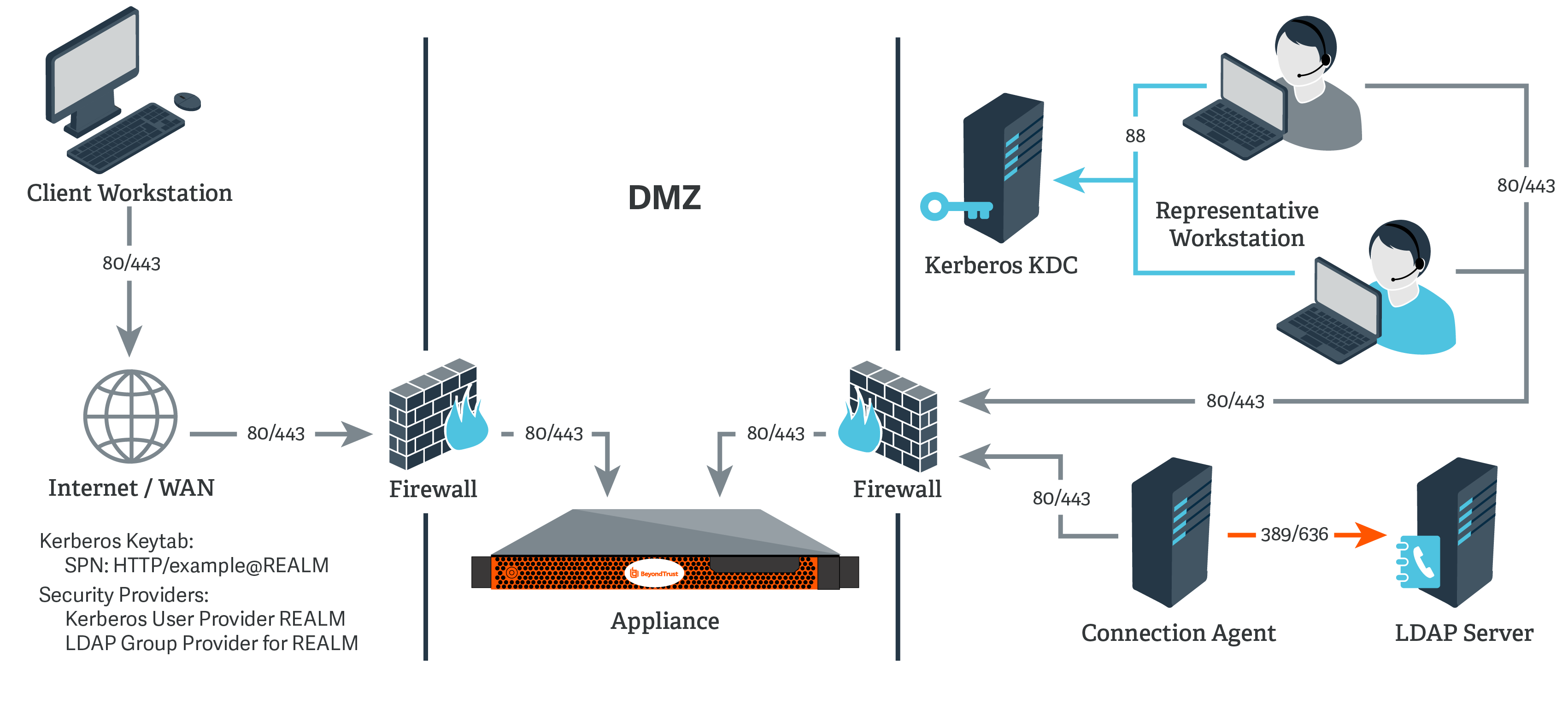
Network Setup Kerberos Kdc And Ldap Server On Separate Networks

Kerberos Authentication Sequence Across Trusts Ace Fekay
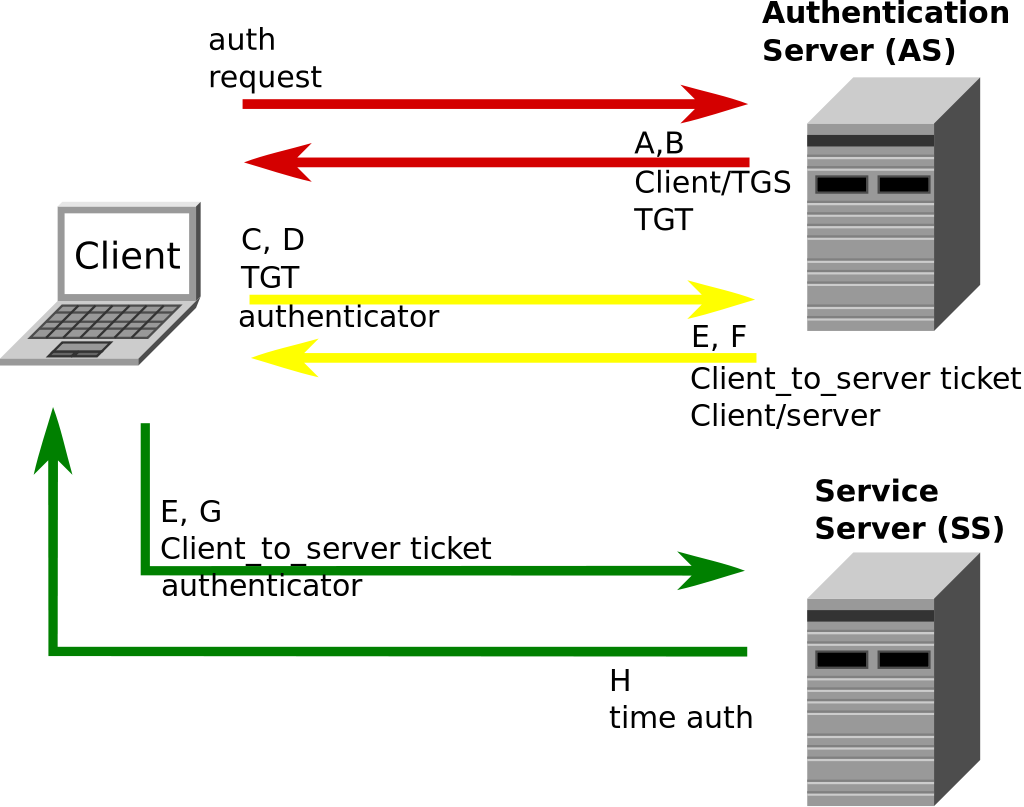
Guide To Step Up Kerberos Single Sign On Sso
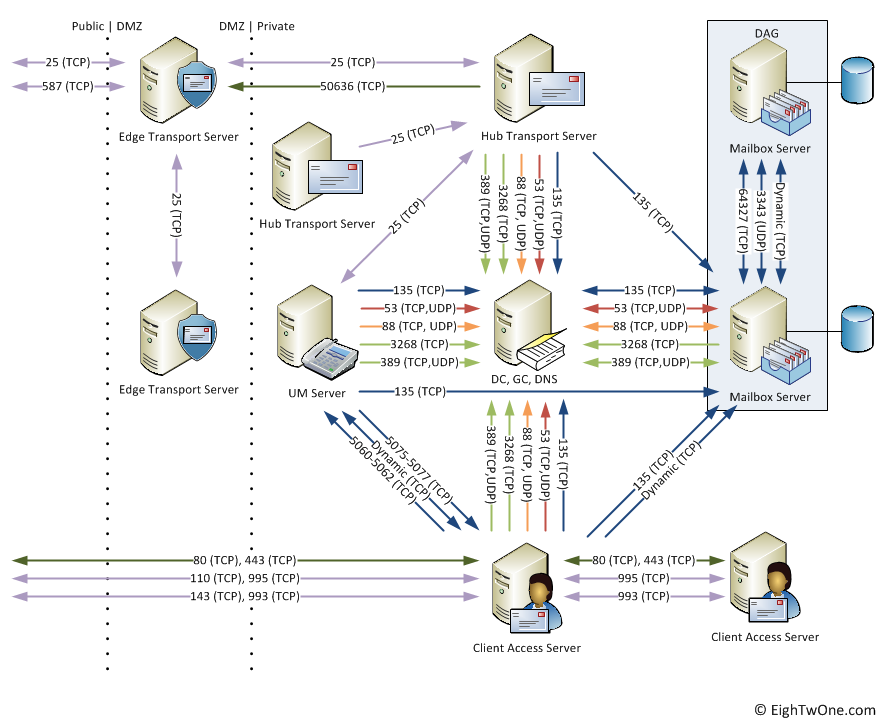
Exchange 2010 Network Ports Eightwone 821

Port 88 Kerberos The Pen Tester Wikipedia
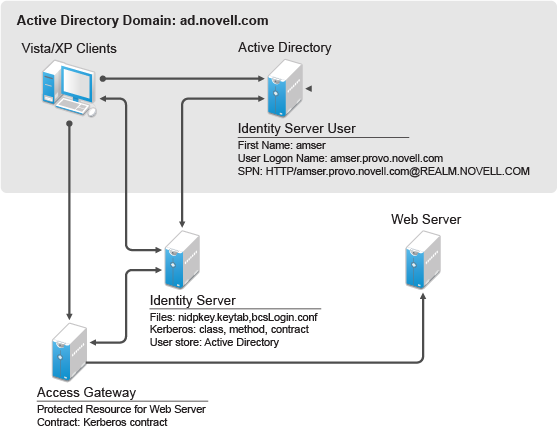
Kerberos Authentication Netiq Access Manager Appliance 4 5 Administration Guide